Threat Spotlight: 3 novel phishing tactics


 As cybercriminals work to make phishing attacks more effective, they are continually introducing new techniques and tactics to try to trick victims, bypass security, and avoid detection.
As cybercriminals work to make phishing attacks more effective, they are continually introducing new techniques and tactics to try to trick victims, bypass security, and avoid detection.
After analyzing data on phishing emails blocked by Barracuda systems during the month of January 2023, Barracuda researchers identified three novel phishing tactics being used by cybercriminals: attacks leveraging Google Translate links, image attachment attacks, and use of special characters in attacks.
While the volume of these attacks is very low — each attack making up less than 1% of phishing attacks detected by Barracuda’s machine learning classifiers — they are widespread, each impacting 11% to 15% of organizations. So, the chances are good that many organizations will run into one of these malicious messages before the end of the year.
What’s important to note is that gateway-based systems provide little to no protection against these types of attacks and would require a lot of tuning and control-based rules to protect customers. These attacks are more dynamic in their nature, where the payload can change upon delivery, as we see prominently in attacks utilizing the Google Translate service.
Let’s take a closer look at these three new tactics, how cybercriminals are using them to evade detection, and what you can do to protect against these types of attacks.
Attacks leveraging Google Translate links
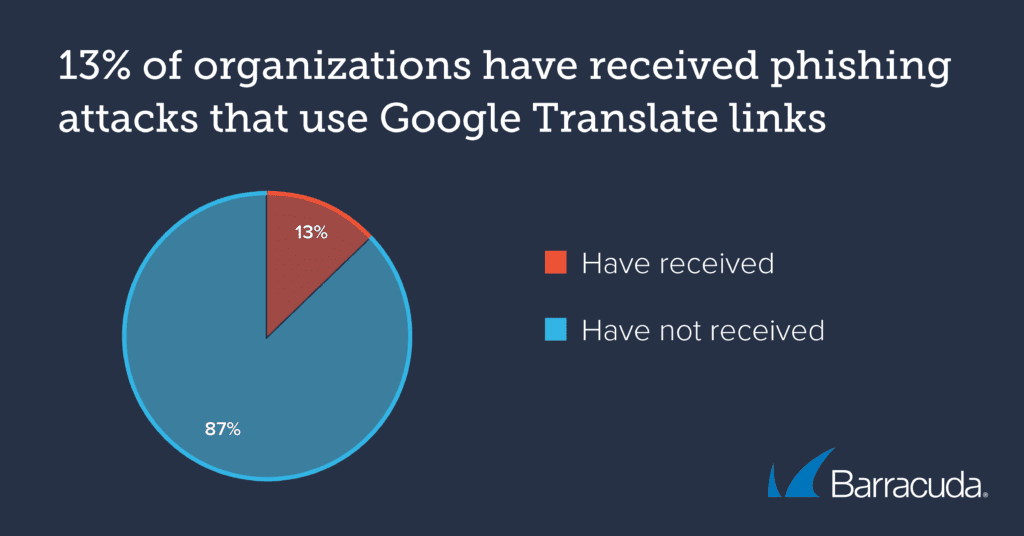
Our researchers are seeing an increasing number of email attacks that use Google Translate services to hide malicious URLs. While only 0.7% of phishing attacks detected by Barracuda’s machine learning classifiers leveraged Google Translate links, 13% of organizations received this type of phishing email. On average, an organization receives roughly 8 of these emails per month.
Attackers use the Google Website Translate feature to send Google-hosted URLs embedded in emails that ultimately lead to phishing websites. This type of attack is commonly referred to as “Google Translate phishing” or simply “Translation-Based Phishing” or “Translation Deception Attack.” In this type of attack, the attacker relies on a translation service to deceive the victim and hide the actual malicious URL. Google Translate is the most widely used service, but our security analysts have also seen similar attacks hosted behind other popular search engines as well.
These attacks are difficult to detect because they contain URLs pointing to a legitimate site. Many email filtering technologies will allow these attacks through into users’ inboxes. When they click on the URLs, users are taken to a fake but authentic-looking website.
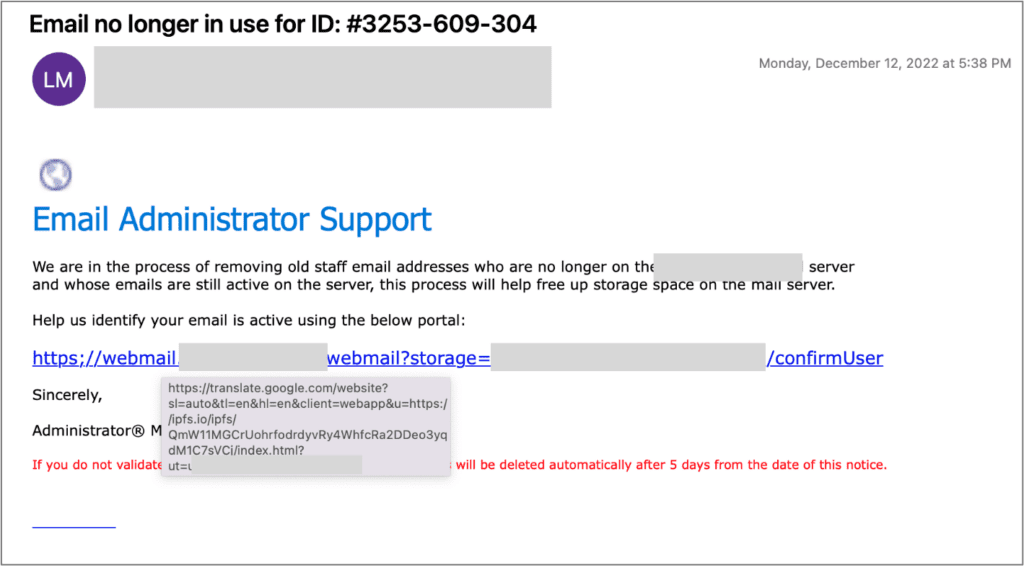
Attackers use translation services to translate a benign URL that is then sent to their victims. The attackers change the payload to malicious content after email delivery, so gateway-based defenses provide little security. Attacks also use poorly formed HTML pages, or a non-supported language, to evade translation. In this case, Google will simply provide a link back to the original URL stating that it is not able to translate the underlying website. Users who mistakenly click on the page will be forwarded to a website under the control of the attacker.
Image attachment attacks
Image based attacks have been commonly used by spammers; however, now attackers are also starting to use images, without any text, in their phishing attacks. These images often include a link or a callback phone number that leads to phishing.
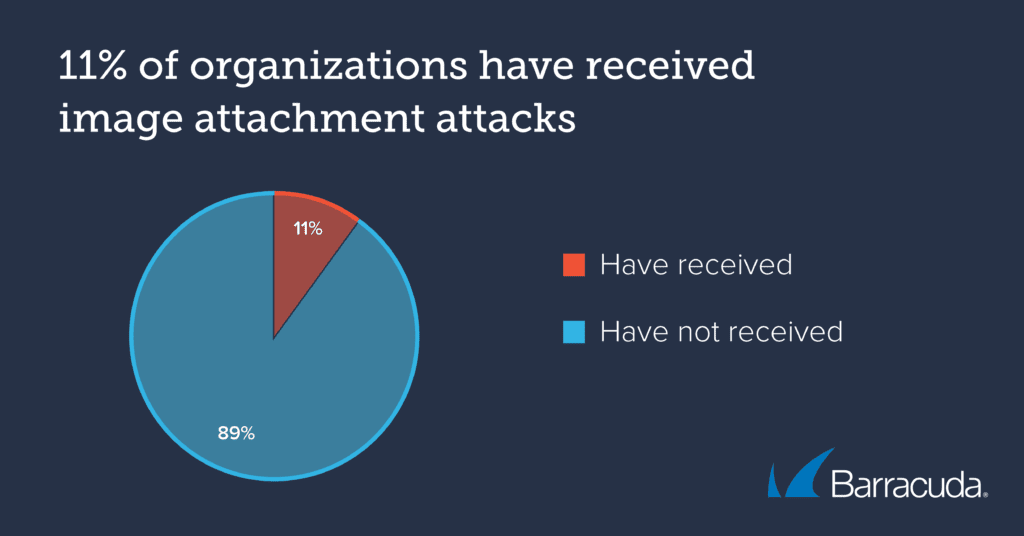
While only 0.2% of phishing attacks detected by Barracuda’s machine learning classifiers were image attachment attacks, 11% of organizations received this type of phishing email. On average, an organization receives around 2 of these emails per month.
Because these attacks do not include any text, traditional email gateway security is not effective at detecting them, which helps attackers get through to their intended victims.
Most of the image attachment attacks Barracuda systems have detected so far have been fake invoices, like the example below.
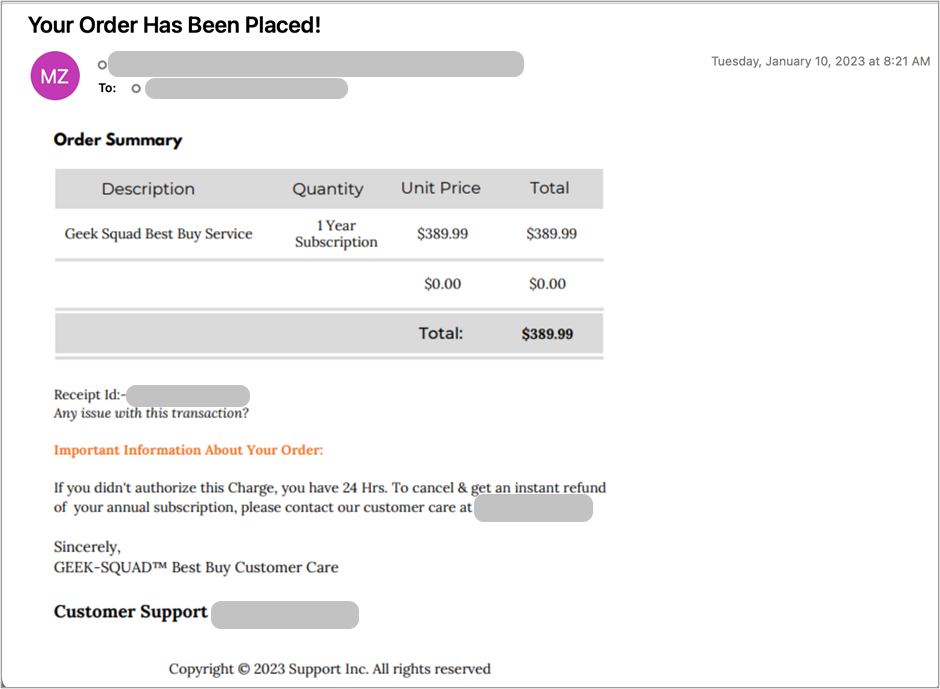
Recently, these types of attacks have become more popularly known as “image phishing” or “phishing by image” attack. They are becoming increasingly popular because users are often more likely to trust an image that appears to come from a legitimate source. As email security measures have become more advanced, cybercriminals have had to develop new tactics to evade detection. Image-based phishing attacks have proven to be an effective technique for bypassing these measures. The use of image-based phishing attacks has grown significantly over the past decade, and it is likely to continue to be a popular tactic for cybercriminals in the future.
Use of special characters in attacks
Hackers often use special characters, such as zero-width Unicode code points, punctuation, non-Latin script, or spaces, to evade detection. While only 0.4% of phishing attacks detected by Barracuda’s machine learning classifiers used this type of attack, Barracuda researchers found that 15% of organizations received phishing emails that used special characters in this way. On average, an organization receives around 4 of these emails per month.
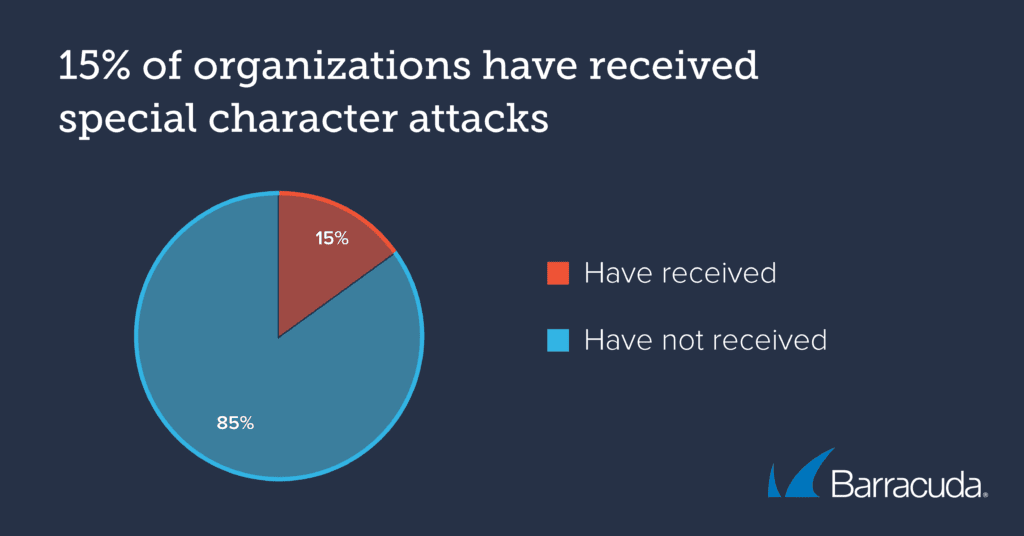
Detection of these attacks can be very difficult because there are legitimate purposes for the use of special characters, such as within email signatures. An email security solution that uses machine learning to detect scam versus benign usage of special characters is the best way to accurately prevent these threats from getting to users.
The example below shows several zero-width characters used by attackers. These characters are not visible to a user receiving a message, but they are visible in HTML code.
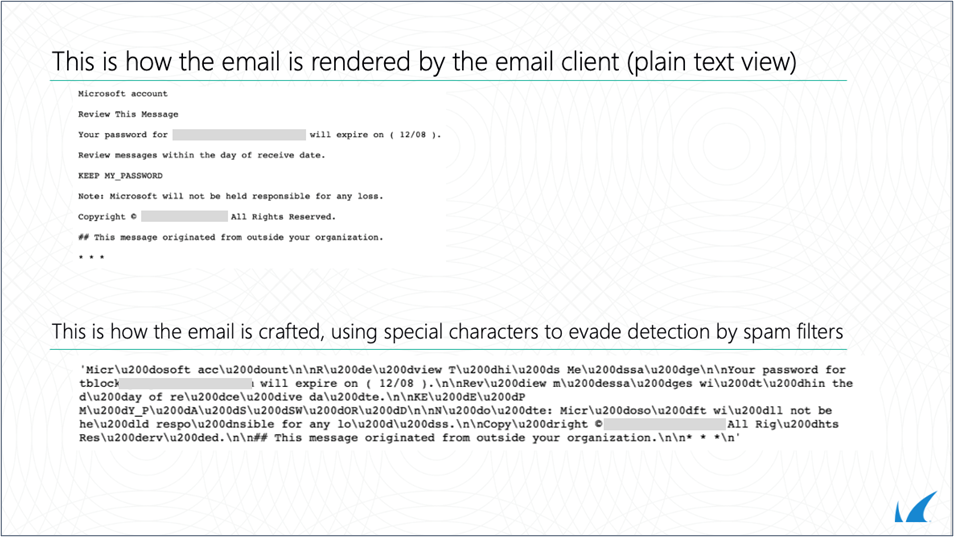
These types of attacks are commonly referred to as “homograph attacks” or simply “zero-width space attacks.” This attack type was commonly used in typo-squatting, where an attacker registers a look-alike domain with special characters to fraud recipients. However, recently, they have become more widely used within the email body as a measure to deceive the recipient into thinking they are seeing emails from a legitimate source.
There are several other attacks similar to these techniques, which we will look at more closely in subsequent blog posts.
- Punycode attacks: Like special or zero-width characters, Punycode attacks utilize non-ASCII characters in domain names to create fake URLs that look identical to legitimate websites and deceive users into entering their username and password, or credit card numbers.
- URL spoofing attacks: These attacks leverage similar domains that may not be entirely identical to actual legitimate websites or businesses. Like Punycode attacks, attackers create sign-in forms where users mistakenly enter their credentials or are prompted to download supposedly secure files, which install ransomware or malware to their local machine.
- Typo-squatting attacks: This is a quite common technique which gateway products provide adequate protection against. In this case, an attack might register a domain like yahooo.com to mimic the real Yahoo! Website.
- Watering hole attacks: In this type of attack, cybercriminals will purposely target a group of users through a compromised site, which is known to be accessed by their target audience. Attackers will inject malicious code into the webpage and use that to steal credentials or other sensitive information, and even install malware or ransomware.
How to protect against these new phishing attacks
- Ensure your email protection scans and blocks malicious links and attachments. These can be hard to identify accurately, and detection often includes a large number of false positives. The best solutions will include machine learning analysis that looks at the image context, the subject of the emails, and combined with sender stats, to determine whether the email is an attack or not.
- Train your users to identify and report potential attacks. Phishing attacks are constantly evolving, so it is important to keep your users informed about new and emerging attack types. Include examples of these attacks as part of your phishing simulation campaigns and train users to always double check before clicking a link or sharing their login credentials.
- If a malicious email did get through, have your post-delivery remediation tools ready to quickly identify and remove any instances of a malicious email from all user inboxes. Automated incident response can help do this quickly before attacks spread through an organization, and account takeover protection can monitor and alert you of suspicious account activity if login credentials were to be compromised.



























